命理網站漏洞(Apache 伺服器未及時更新)
self-signed
Country
|
Taiwan
|
Organization
|
Digital
United
|
ISP
|
Digital
United
|
Last Update
|
2020-05-06T16:13:31.351863
|
ASN
|
AS4780
|
Web Technologies
Vulnerabilities
Note: the
device may not be impacted by all of these issues. The vulnerabilities are
implied based on the software and version.
CVE-2014-0117
|
The mod_proxy
module in the Apache HTTP Server 2.4.x before 2.4.10, when a reverse proxy is
enabled, allows remote attackers to cause a denial of service (child-process
crash) via a crafted HTTP Connection header.
|
CVE-2014-0118
|
The
deflate_in_filter function in mod_deflate.c in the mod_deflate module in the
Apache HTTP Server before 2.4.10, when request body decompression is enabled,
allows remote attackers to cause a denial of service (resource consumption)
via crafted request data that decompresses to a much larger size.
|
CVE-2016-0736
|
In Apache HTTP
Server versions 2.4.0 to 2.4.23, mod_session_crypto was encrypting its
data/cookie using the configured ciphers with possibly either CBC or ECB
modes of operation (AES256-CBC by default), hence no selectable or builtin
authenticated encryption. This made it vulnerable to padding oracle attacks,
particularly with CBC.
|
CVE-2015-3185
|
The
ap_some_auth_required function in server/request.c in the Apache HTTP Server
2.4.x before 2.4.14 does not consider that a Require directive may be
associated with an authorization setting rather than an authentication
setting, which allows remote attackers to bypass intended access restrictions
in opportunistic circumstances by leveraging the presence of a module that
relies on the 2.2 API behavior.
|
CVE-2015-3184
|
mod_authz_svn
in Apache Subversion 1.7.x before 1.7.21 and 1.8.x before 1.8.14, when using
Apache httpd 2.4.x, does not properly restrict anonymous access, which allows
remote anonymous users to read hidden files via the path name.
|
CVE-2018-1312
|
In Apache
httpd 2.2.0 to 2.4.29, when generating an HTTP Digest authentication
challenge, the nonce sent to prevent reply attacks was not correctly
generated using a pseudo-random seed. In a cluster of servers using a common
Digest authentication configuration, HTTP requests could be replayed across
servers by an attacker without detection.
|
CVE-2014-0098
|
The log_cookie
function in mod_log_config.c in the mod_log_config module in the Apache HTTP
Server before 2.4.8 allows remote attackers to cause a denial of service (segmentation
fault and daemon crash) via a crafted cookie that is not properly handled
during truncation.
|
CVE-2016-8612
|
Apache HTTP
Server mod_cluster before version httpd 2.4.23 is vulnerable to an Improper
Input Validation in the protocol parsing logic in the load balancer resulting
in a Segmentation Fault in the serving httpd process.
|
CVE-2014-0226
|
Race condition
in the mod_status module in the Apache HTTP Server before 2.4.10 allows
remote attackers to cause a denial of service (heap-based buffer overflow),
or possibly obtain sensitive credential information or execute arbitrary
code, via a crafted request that triggers improper scoreboard handling within
the status_handler function in modules/generators/mod_status.c and the
lua_ap_scoreboard_worker function in modules/lua/lua_request.c.
|
CVE-2014-3523
|
Memory leak in
the winnt_accept function in server/mpm/winnt/child.c in the WinNT MPM in the
Apache HTTP Server 2.4.x before 2.4.10 on Windows, when the default
AcceptFilter is enabled, allows remote attackers to cause a denial of service
(memory consumption) via crafted requests.
|
CVE-2017-15710
|
In Apache
httpd 2.0.23 to 2.0.65, 2.2.0 to 2.2.34, and 2.4.0 to 2.4.29,
mod_authnz_ldap, if configured with AuthLDAPCharsetConfig, uses the
Accept-Language header value to lookup the right charset encoding when
verifying the user's credentials. If the header value is not present in the
charset conversion table, a fallback mechanism is used to truncate it to a
two characters value to allow a quick retry (for example, 'en-US' is
truncated to 'en'). A header value of less than two characters forces an out
of bound write of one NUL byte to a memory location that is not part of the
string. In the worst case, quite unlikely, the process would crash which
could be used as a Denial of Service attack. In the more likely case, this
memory is already reserved for future use and the issue has no effect at all.
|
CVE-2017-15715
|
In Apache
httpd 2.4.0 to 2.4.29, the expression specified in <FilesMatch> could
match '$' to a newline character in a malicious filename, rather than
matching only the end of the filename. This could be exploited in
environments where uploads of some files are are externally blocked, but only
by matching the trailing portion of the filename.
|
CVE-2013-6438
|
The
dav_xml_get_cdata function in main/util.c in the mod_dav module in the Apache
HTTP Server before 2.4.8 does not properly remove whitespace characters from
CDATA sections, which allows remote attackers to cause a denial of service
(daemon crash) via a crafted DAV WRITE request.
|
CVE-2017-7679
|
In Apache
httpd 2.2.x before 2.2.33 and 2.4.x before 2.4.26, mod_mime can read one byte
past the end of a buffer when sending a malicious Content-Type response
header.
|
CVE-2018-17199
|
In Apache HTTP
Server 2.4 release 2.4.37 and prior, mod_session checks the session expiry
time before decoding the session. This causes session expiry time to be
ignored for mod_session_cookie sessions since the expiry time is loaded when
the session is decoded.
|
CVE-2017-9788
|
In Apache
httpd before 2.2.34 and 2.4.x before 2.4.27, the value placeholder in
[Proxy-]Authorization headers of type 'Digest' was not initialized or reset
before or between successive key=value assignments by mod_auth_digest.
Providing an initial key with no '=' assignment could reflect the stale value
of uninitialized pool memory used by the prior request, leading to leakage of
potentially confidential information, and a segfault in other cases resulting
in denial of service.
|
CVE-2014-8109
|
mod_lua.c in
the mod_lua module in the Apache HTTP Server 2.3.x and 2.4.x through 2.4.10
does not support an httpd configuration in which the same Lua authorization
provider is used with different arguments within different contexts, which
allows remote attackers to bypass intended access restrictions in
opportunistic circumstances by leveraging multiple Require directives, as
demonstrated by a configuration that specifies authorization for one group to
access a certain directory, and authorization for a second group to access a
second directory.
|
CVE-2017-9798
|
Apache httpd
allows remote attackers to read secret data from process memory if the Limit
directive can be set in a user's .htaccess file, or if httpd.conf has certain
misconfigurations, aka Optionsbleed. This affects the Apache HTTP Server
through 2.2.34 and 2.4.x through 2.4.27. The attacker sends an
unauthenticated OPTIONS HTTP request when attempting to read secret data.
This is a use-after-free issue and thus secret data is not always sent, and
the specific data depends on many factors including configuration.
Exploitation with .htaccess can be blocked with a patch to the
ap_limit_section function in server/core.c.
|
CVE-2016-2161
|
In Apache HTTP
Server versions 2.4.0 to 2.4.23, malicious input to mod_auth_digest can cause
the server to crash, and each instance continues to crash even for
subsequently valid requests.
|
CVE-2014-0231
|
The mod_cgid
module in the Apache HTTP Server before 2.4.10 does not have a timeout
mechanism, which allows remote attackers to cause a denial of service
(process hang) via a request to a CGI script that does not read from its
stdin file descriptor.
|
CVE-2013-4352
|
The
cache_invalidate function in modules/cache/cache_storage.c in the mod_cache
module in the Apache HTTP Server 2.4.6, when a caching forward proxy is
enabled, allows remote HTTP servers to cause a denial of service (NULL
pointer dereference and daemon crash) via vectors that trigger a missing
hostname value.
|
CVE-2019-0220
|
A
vulnerability was found in Apache HTTP Server 2.4.0 to 2.4.38. When the path
component of a request URL contains multiple consecutive slashes ('/'),
directives such as LocationMatch and RewriteRule must account for duplicates
in regular expressions while other aspects of the servers processing will
implicitly collapse them.
|
CVE-2016-4975
|
Possible CRLF
injection allowing HTTP response splitting attacks for sites which use
mod_userdir. This issue was mitigated by changes made in 2.4.25 and 2.2.32
which prohibit CR or LF injection into the "Location" or other
outbound header key or value. Fixed in Apache HTTP Server 2.4.25 (Affected
2.4.1-2.4.23). Fixed in Apache HTTP Server 2.2.32 (Affected 2.2.0-2.2.31).
|
CVE-2018-1283
|
In Apache
httpd 2.4.0 to 2.4.29, when mod_session is configured to forward its session
data to CGI applications (SessionEnv on, not the default), a remote user may
influence their content by using a "Session" header. This comes
from the "HTTP_SESSION" variable name used by mod_session to
forward its data to CGIs, since the prefix "HTTP_" is also used by
the Apache HTTP Server to pass HTTP header fields, per CGI specifications.
|
CVE-2016-8743
|
Apache HTTP
Server, in all releases prior to 2.2.32 and 2.4.25, was liberal in the
whitespace accepted from requests and sent in response lines and headers.
Accepting these different behaviors represented a security concern when httpd
participates in any chain of proxies or interacts with back-end application
servers, either through mod_proxy or using conventional CGI mechanisms, and
may result in request smuggling, response splitting and cache pollution.
|
Ports
·
25
·
80
·
443
Services
220 web2.ncc.com.tw ESMTP Postfix
250-web2.ncc.com.tw
250-PIPELINING
250-SIZE 10240000
250-VRFY
250-ETRN
250-ENHANCEDSTATUSCODES
250-8BITMIME
250 DSN
Apache httpdVersion: 2.4.6
HTTP/1.1 301 Moved Permanently
Date: Wed, 06 May 2020 16:13:22 GMT
Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9
PHP/7.2.30
Location: https://210.68.113.216/
Content-Length: 231
Content-Type: text/html; charset=iso-8859-1
Apache httpdVersion: 2.4.6
HTTP/1.1 403 Forbidden
Date: Wed, 06 May 2020 16:13:31 GMT
Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9
PHP/7.2.30
Last-Modified: Thu, 16 Oct 2014 13:20:58 GMT
ETag: "1321-5058a1e728280"
Accept-Ranges: bytes
Content-Length: 4897
Vary: Accept-Encoding
Content-Type: text/html; charset=UTF-8
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 28413
(0x6efd)
Signature Algorithm:
sha256WithRSAEncryption
Issuer: C=--, ST=SomeState,
L=SomeCity, O=SomeOrganization, OU=SomeOrganizationalUnit,
CN=web1/emailAddress=root@web1
Validity
Not Before: May 23
06:16:48 2018 GMT
Not After : May 23
06:16:48 2019 GMT
Subject: C=--, ST=SomeState,
L=SomeCity, O=SomeOrganization, OU=SomeOrganizationalUnit,
CN=web1/emailAddress=root@web1
Subject Public Key Info:
Public Key Algorithm:
rsaEncryption
Public-Key: (2048
bit)
Modulus:
00:e4:7e:bb:c1:c6:1d:9d:bd:a2:81:3f:9b:b3:ea:
0b:a4:6e:1d:16:aa:85:c6:3b:bb:c4:80:ed:91:ce:
7d:f5:7c:1c:81:cc:5c:c5:51:23:56:20:4f:aa:5f:
fb:a2:ac:82:37:4b:91:9f:c3:70:c8:8c:c1:78:a6:
56:32:36:e1:63:2c:be:07:1e:ed:2d:cd:85:6c:50:
a9:d4:12:77:46:49:e1:c9:9c:8e:fd:de:a2:11:cf:
43:99:13:0d:e7:5e:cd:bf:4d:99:1b:f5:f7:b8:48:
46:14:ff:fc:9d:40:b3:ed:59:c9:87:f7:f2:cc:ca:
4a:ae:5d:da:0b:0c:0b:3a:bf:1f:bd:f9:4a:81:9c:
1c:67:08:36:ae:5d:0a:23:4b:5d:ee:c6:f0:d4:a5:
3a:c8:d0:a5:db:94:ec:17:3d:cf:54:36:15:47:b3:
0a:29:b4:a3:41:2e:cc:45:ff:cf:bf:6f:dd:88:99:
31:14:f1:82:ee:94:7a:8b:8c:f9:a2:02:7c:34:3a:
b2:58:6b:a1:f8:a8:93:b0:8b:ed:df:69:da:a6:bb:
75:56:26:9c:cd:08:bf:49:38:0c:b4:2a:a4:9c:19:
db:de:3b:c1:95:8c:bf:f2:10:35:af:7a:c7:66:5a:
48:aa:4e:5e:90:44:44:aa:f7:bb:6b:c7:c5:a4:93:
25:8f
Exponent: 65537
(0x10001)
X509v3 extensions:
X509v3 Basic
Constraints:
CA:FALSE
X509v3 Key Usage:
Digital Signature,
Non Repudiation, Key Encipherment
Signature Algorithm:
sha256WithRSAEncryption
c6:bd:fd:ff:4d:82:d5:c5:9e:0d:ab:fd:3b:d0:bb:13:e7:90:
f7:b0:1e:53:f7:df:ee:1e:05:a4:44:18:7d:48:1f:fc:67:1e:
19:c2:83:c1:27:0b:65:97:14:15:68:86:13:a3:c9:6b:3f:b5:
ed:84:d1:f6:d0:6d:5b:33:06:1d:e1:be:f9:ca:6d:5b:70:d5:
81:73:0c:7d:7c:f5:50:41:eb:38:9d:81:5f:d1:93:94:e9:bb:
9f:94:1f:72:1f:d0:5d:00:a7:07:d0:a2:55:f3:cf:aa:73:55:
91:48:67:ec:92:fb:6d:e6:15:1f:d4:8d:cd:ae:a8:e7:3e:a1:
0e:93:5d:b3:5c:43:9a:42:cc:97:b5:57:ea:16:ec:b0:72:e3:
b2:43:ce:45:33:30:b7:40:bd:32:9b:e6:e8:dd:8a:64:ac:ce:
33:5c:32:a0:ee:64:d1:9e:fa:f8:50:cd:f3:a3:eb:25:9c:7e:
14:12:1c:43:47:ce:60:f7:6c:69:72:0a:89:ae:46:ef:ab:b3:
22:85:c1:b7:dd:3c:6f:ff:bd:59:40:e2:bd:ef:24:cb:e6:e4:
d5:9f:15:ac:69:bf:9d:85:3f:5d:48:ec:26:0c:a4:a5:b5:70:
53:18:e0:7f:4e:21:72:79:58:a7:a1:6b:22:c7:75:58:27:aa:
04:58:ab:26

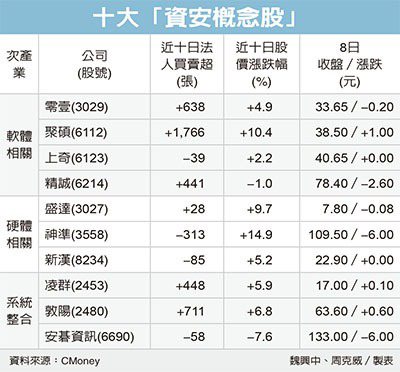 經濟日報提供法人表示,疫情造就各項新科技類股崛起,也突顯出資安的重要性。愈來愈多企業與個人透過網路收集、處理、儲存及傳送大量訊息,當中部分為保密數據,網路資安的重要性與日俱增。
經濟日報提供法人表示,疫情造就各項新科技類股崛起,也突顯出資安的重要性。愈來愈多企業與個人透過網路收集、處理、儲存及傳送大量訊息,當中部分為保密數據,網路資安的重要性與日俱增。 中油加油站。(記者黃佩君攝)
中油加油站。(記者黃佩君攝)